Defense agencies and contractors alike are entrusted with information that must be safeguarded and protected to the highest degree. The management of outdated computers and other unwanted IT equipment must be handled with care, as equipment improperly disposed of could easily have its secrets revealed if it ends up in the wrong hands.
In 2014, a 25-year-old British man broke into the satellite communication system of the U.S. Defense Department and stole information from more than 30,000 satellite phones and 800 employee user accounts. According to IT News, the data breach cost $628,000 to rectify.
If this is the extent of damage that can be done by a cyberhacker gaining access to the military’s systems from an off-site computer, imagine the damage that could be caused by a troublemaker having an obsolete military computer or another former piece of Defense IT assets in their physical possession.
The potential damage is mind-boggling, and could have catastrophic results if particularly sensitive information was leaked to outside groups.
And then there was the time a top-level U.S. Defense contractor left a cache of more than 60,000 classified files on an Amazon server with no password protection. The classified data included unencrypted passwords and security credential for government contractors.
Security of Defense IT Assets is of Paramount Importance
It goes without saying that computers, servers, hard drives, and other IT assets that have ever been utilized by any sector of the Defense must be safeguarded. It is simply not enough to erase the data from an unwanted hard drive and sell or dispose of it.
If hackers can gain access to U.S. Defense’s enhanced mobile satellite services system, the international system used to relay messages between military employees via satellite around the world, then they can certainly recover sensitive data that was purportedly “erased” from a now-obsolete hard drive. Because, as is now becoming more evident, the simple press of the delete button erases far less than is commonly thought.

Certified Data Destruction Services
It is only with certified data destruction services that comply with the strictest standards that contractors and other sectors can guarantee military-grade data destruction solutions. All Green Recycling operates to the National Institute for Standards and Technology’s (NIST) Special Publication 800-88: Guidelines for Media Sanitization: the real-world reference for data erasure compliance that recently replaced the more commonly known Department of Defense 5220.22-M standard.
NIST 800-88: Guidelines for Media Sanitization
The National Institute for Standards and Technology’s (NIST) Guidelines for Media Sanitization give clear guidance as to how information should be protected and media devices sanitized at the end of the media’s useful life.
As shown in the flowchart below, the decision is primarily based on the level of confidentiality of the information contained on the media, and secondly by the type of media device itself.
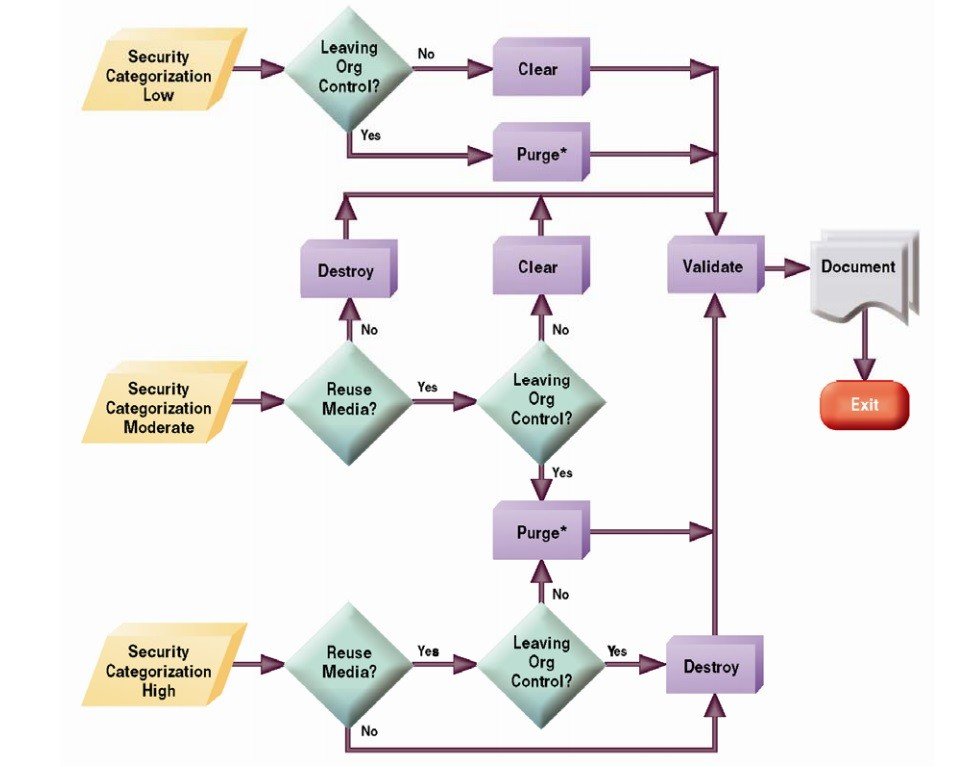
Image courtesy NIST
Defense Sectors Served
- United States Defense Contractors
- United States Military
- Homeland Security
- NASA Contractors
- Private Military Contractors
- Government Contractors
- Law Enforcement
Find Out More
To find out more about All Green Recycling’s commitment to assisting the Defense sectors in maintaining the utmost security for their IT assets and other equipment, contact us today.










